Bold Reports® Installation and Deployment on Ubuntu for v6.1 or later
Deployment prerequisites
-
Access to a Linux server with a standard user account and sudo privileges.
-
Install
Nginxby running the following commands:sudo apt-get updatesudo apt-get install nginx -
Install
zipby running the following commandsudo apt-get install zip -
Install
GDIPluspackage using the following command.sudo apt-get install libgdiplus -
Install the
python 3.9 or laterby executing the following command:Ubuntu Version:22.04 :
sudo apt-get install -y python3Ubuntu Version:20.04 :
sudo apt update && sudo apt install wget software-properties-common && sudo add-apt-repository ppa:deadsnakes/ppa && sudo apt update && sudo apt install python3.9 -
Install pip dependency packages for ETL service by running the following command:
sudo apt-get install python3-pip && sudo python3 -m pip install --upgrade pip && sudo pip install duckdb===1.1.2 dlt===0.4.12 pymysql pyodbc pg8000 poetry pandas===2.2.2 numpy===1.26.4 "dlt[parquet]" "dlt[filesystem]" -
Add an
openssl confpath in the environment if it does not exist.export OPENSSL_CONF=/etc/ssl/
Configuring the Bold Reports® application
-
Register and download the Bold Reports® Linux package from here.
-
Download the Bold Reports® Linux package by running the following command:
sudo wget {Bold Reports Linux package link} -
Extract the zip file by running the following command:
sudo unzip {Bold Reports Linux package zip file} -
Change the directory to
BoldReports_EnterpriseReporting-Linuxby running the following command:cd BoldReports_EnterpriseReporting-Linux -
Execute the following command to deploy Bold Reports® on your Linux machine.
sudo bash install-boldreports.sh -i {new} -u {user} -h {host URL} -n {true or false}-
i: Installation type : Specifies either it is a new or upgrade installation.
-
u: Specify the user or group that manages the service.
-
h: Domain or IP address of the machine with HTTP protocol.
-
n: Setting this to
truewill automatically configure the Bold Reports® with the Nginx front-end server.
IMPORTANT: If you have any existing applications running on that Linux machine using Nginx, set “-n” value to false and configure Nginx manually.
Example for a new installation,
sudo bash install-boldreports.sh -i new -u www-data -h http://linux.example.com -n true -
-
If you are using Bold Reports® version 11.1.10 or above and if you want to use a HTTPS domain with SSL configuration, execute the following command to deploy Bold Reports® along with SSL configuration.
sudo bash install-boldreports.sh -i {new} -u {user} -h {host URL} -n {true or false} --ssl-cert {ssl certificate path} --ssl-key {ssl key path}IMPORTANT: It is mandatory to give paths for SSL certificate and key in —ssl-cert and —ssl-key. If paths are not given or if the given path does not exist, then the installation will be stopped.
-
ssl-cert: Specify the path in which the SSL certificate is present.
-
ssl-key: Specify the path in which the SSL key is present.
Example for a new installation with SSL configuration,
sudo bash install-boldreports.sh -i new -u www-data -h https://linux.example.com -n true --ssl-cert /etc/ssl/domain.crt --ssl-key /etc/ssl/domain.key -
Once the installation is complete, open the host URL in the browser and continue the application startup.
Manually configure Nginx
To configure Nginx as a reverse proxy to forward requests to the Bold Reports® app, modify /etc/nginx/sites-available/default. Open it in a text editor and add the following code:
#server {
#listen 80;
#server_name example.com;
#return 301 https://example.com$request_uri;
#}
server {
listen 80 default_server;
#server_name example.com;
#listen 443 ssl;
#ssl on;
#ssl_certificate /path/to/certificate/file/domain.crt;
#ssl_certificate_key /path/to/key/file/domain.key;
proxy_read_timeout 300;
proxy_connect_timeout 300;
proxy_send_timeout 300;
send_timeout 300;
client_max_body_size 200M;
location / {
root /var/www/bold-services/application/idp/web/wwwroot;
proxy_pass http://localhost:6500/;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection keep-alive;
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
fastcgi_buffers 16 16k;
fastcgi_buffer_size 32k;
}
location /api {
proxy_pass http://localhost:6501/api;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection keep-alive;
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /ums {
root /var/www/bold-services/application/idp/ums/wwwroot;
proxy_pass http://localhost:6502/ums;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection keep-alive;
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /ums/signalr/progresshub {
proxy_pass http://localhost:6502/ums/signalr/progresshub;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /reporting {
root /var/www/bold-services/application/reporting/web/wwwroot;
proxy_pass http://localhost:6550/reporting;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection keep-alive;
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /reporting/messageHub {
proxy_pass http://localhost:6550/reporting/messageHub;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /reporting/api {
proxy_pass http://localhost:6551/reporting/api;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection keep-alive;
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /reporting/jobs {
proxy_pass http://localhost:6552/reporting/jobs;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection keep-alive;
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /reporting/reportservice {
root /var/www/bold-services/application/reporting/reportservice;
proxy_pass http://localhost:6553;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection keep-alive;
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /reporting/viewer {
proxy_pass http://localhost:6554/reporting/viewer;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection keep-alive;
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /etlservice/ {
root /var/www/bold-services/application/etl/etlservice/wwwroot;
proxy_pass http://localhost:6509/;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $http_host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /etlservice/_framework/blazor.server.js {
root /var/www/bold-services/application/etl/etlservice/wwwroot;
proxy_pass http://localhost:6509/_framework/blazor.server.js;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $http_host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
}Once the Nginx configuration is established, run sudo nginx -t to verify the syntax of the configuration files. If the configuration file test is successful, force Nginx to pick up the changes by running the sudo nginx -s reload.
Configure SSL
Follow the below steps only in either of the two cases:
-
If you have set the “-n” value to false along with HTTPS domain and manually configured Nginx during initial deployment.
-
If you have deployed Bold Reports® application using HTTP domain and now want to change the domain as HTTPS.
Otherwise, you can skip this section.
Steps to follow for SSL configuration:
-
Uncomment the following marked lines in the Nginx config file.
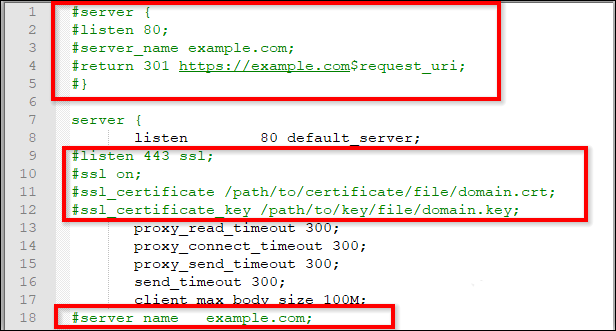
-
Comment on the following marked line in the Nginx config file.
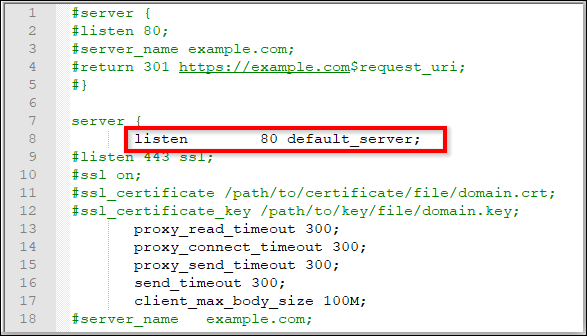
-
Replace
example.comwith your domain name. -
Define the path of the SSL certificate:
ssl_certificate /etc/ssl/domain.crt. -
Specify the directory where the SSL certificate key is located:
ssl_certificate_key /etc/ssl/domain.key. -
Save and run sudo
nginx -tto verify the syntax of the configuration file. If the configuration file test is successful, force Nginx to pick up the changes by runningsudo nginx -s reload. -
Navigate to the proxy settings page of the UMS application ({domain_name}/ums/administration/proxy-settings) and update the Site URL as shown in the following image with new domain.
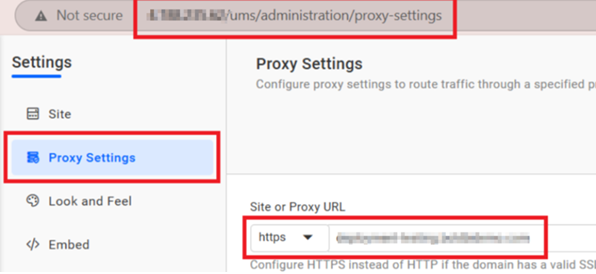
-
You can ignore SSL certificate errors by checking the checkbox for ignoring the SSL certificate errors.
-
Check the checkbox for update the URL as shown in the below image and save the proxy settings by clicking on Save button.
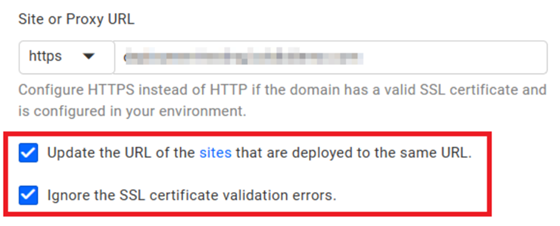
-